The Cybersecurity Maturity Model Certification (CMMC) is a crucial program for defense contractors. CMMC Level 2, referred to as Advanced, applies to the 80,000 organizations that handle Controlled Unclassified Information (CUI). It aligns with the existing Defense Federal Acquisition Regulation Supplement (DFARS) 7012 requirement by mandating that CUI be protected using the 110 controls defined in NIST SP 800-171.
This comprehensive guide provides insights into CMMC Level 2, its key requirements, and how to achieve compliance.
CMMC 2.0: Level 2 (Advanced) Requirements
Under CMMC 2.0, the ‘Advanced’ level (Level 2) has five key requirements.
1) Protect CUI Using NIST SP 800-171 Controls
Contractors must protect CUI using the 110 controls specified in NIST SP 800-171. These controls are grouped into 14 families of security requirements, which are further broken into 320 specific security objectives. For a deeper understanding of NIST SP 800-171, read our blog.
2) Compliance Will Be Determined via Third-Party Assessments
CMMC Level 2 requires a CMMC Third Party Assessment Organization (C3PAO) to validate compliance with NIST SP 800-171 controls. The fundamental purpose of the CMMC program is to avoid reliance on self-assessments.
3) FedRAMP Baseline Moderate:
The cloud service must be FedRAMP Baseline Moderate Equivalent or have an Authorization to Operate (ATO). Contractors must determine if their cloud service meets the FedRAMP requirement by either checking the FedRAMP marketplace for an ATO or seeking a letter of attestation for FedRAMP Equivalence from a certified FedRAMP 3PAO. The US Department of Defense has established the requirements for FedRAMP equivalence in this memo.
4) FIPS 140-2 Encryption:
CUI must be encrypted using cryptographic modules validated to meet Federal Information Processing Standards (FIPS) 140-2. Organizations should seek a validation certificate from the cloud service and verify it on the NIST website.
5) Incident Reporting:
Contractors must ensure that the cloud service complies with DFARS 7012 (c-g) requirements, including cyber incident reporting, malicious software handling, and media preservation and protection.
Learn more about achieving CMMC compliance below:
CMMC Relationship to DFARS 7012
CMMC and DFARS 7012 both establish the same compliance requirements for CUI. However, DFARS, which contractors must already comply with to fulfill their existing contracts, allows for self-assessments. In contrast, CMMC mandates evaluations by third-party assessors. This change addresses the deficiencies observed under DFARS, where self-assessments often led to inadequate protection of CUI.
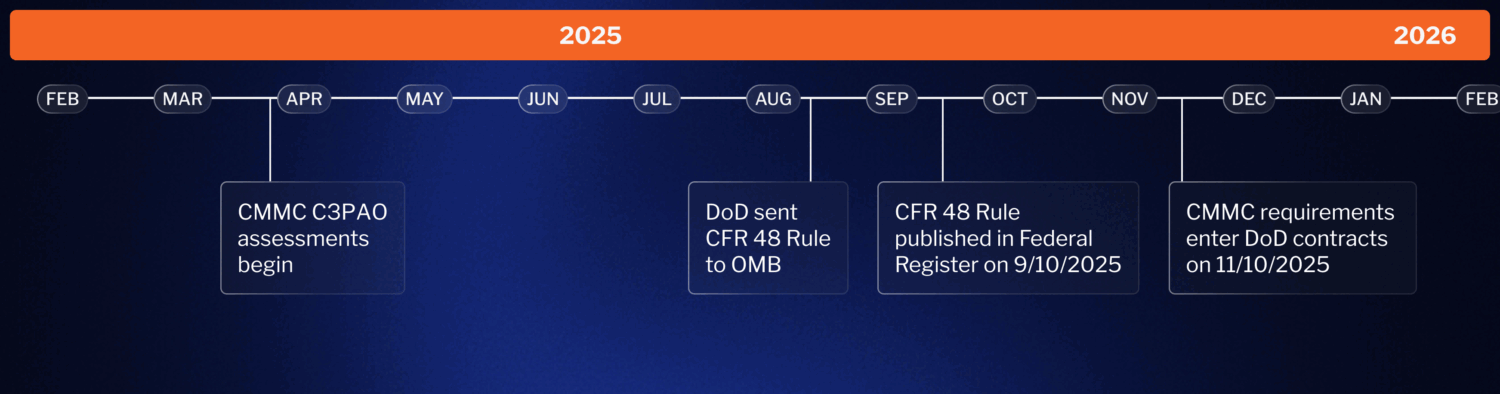
CMMC Timeline
The CMMC Final Rule has been published and became effective on December 16, 2024. In addition, C3PAO-led CMMC assessments began in January of this year 2025 . Upcoming on the CMMC timeline, the DoD will gradually increase the number of programs with CMMC requirements over 4 years, culminating in all applicable contracts requiring CMMC compliance.
Consequences of Non-Compliance with CMMC
Contractors without a CMMC certification from a C3PAO will be ineligible for contract awards, ensuring that contractors take their responsibility to protect CUI seriously.
It is important to understand that even though CMMC will be phased in over time, it does not necessarily follow that you have more time to achieve CMMC certification. Your organization, for example, could be far down the supply chain from a contractor subject to CMMC in Phase 1, in which case that contractor must flow down CMMC requirements to your organization at that time.
CMMC Certification Duration and Reaffirmation Requirements
A CMMC Level 2 certification will last for three years. However, organizations must reaffirm their ongoing compliance annually. This reaffirmation must be formally signed off by a senior executive of the organization.
Level 2 compliance is not a one-time event; instead, CMMC requires ongoing revalidation. This requires updating compliance documentation and IT systems post-assessment. The executive reaffirmation will serve as a serious validation of ongoing compliance, with non-compliance or false declarations carrying legal consequences.
CMMC Assessment Guide
CMMC has a scoring system for each control based on the NIST SP 800-171A Assessment Methodology. Each of the 110 controls in NIST SP 800-171 is assigned a point value, leading to a total possible score of 110 points. However, due to the weighting of different controls, the actual point value for each control can vary significantly.
To be certified, an organization must achieve a minimum score of 88, which represents 80% compliance. However, it is crucial to understand that certain critical controls must be fully implemented. Here’s a breakdown:
1. Critical Controls:
These controls have higher point values and are considered foundational. Missing even one critical control can result in a significant reduction in the overall score and can disqualify an organization from certification. All critical controls must be met to achieve the minimum score.
2. Non-Critical Controls:
These controls generally have fewer points assigned to them but are still essential for a comprehensive security posture. Some of these controls can be part of the unmet controls, provided they do not cause the score to drop below 88 points.
Points are deducted for each unmet control, and the deductions can range from 1 to 5 points per control. Critical controls might result in larger deductions if not implemented.
Limited Duration Plan of Action and Milestones (POA&M) Allowed
CMMC 2.0 allows an organization to be compliant without a perfect 110 score. Unmet controls must be documented with a timeline for implementation in a Plan of Action and Milestones (POA&M). These POA&Ms must be addressed within 180 days of certification. This approach makes compliance more achievable without requiring perfection, especially for small and medium-sized businesses (SMBs).
In summary, achieving a minimum score of 88 is mandatory for CMMC Level 2 certification, but organizations must ensure all critical controls are implemented and have a clear plan for addressing any remaining gaps within the allowed timeframe.
CMMC Compliance Documentation Requirements
To demonstrate compliance, an organization must prepare detailed documents on how it protects CUI and ensure that personnel are trained to follow the appropriate policies and procedures necessary to secure CUI. The primary documents include:
1. System Security Plan (SSP):
The SSP document outlines the organization’s security posture, detailing the implementation of the 110 controls from NIST SP 800-171. The SSP should cover all aspects of the IT environment, including hardware, software, policies, and procedures.
2. Standard Operating Procedures (SOPs):
These documents provide step-by-step instructions on how specific security tasks are to be performed. SOPs ensure consistency in security practices and help personnel understand their roles and responsibilities in maintaining cybersecurity.
3. Plan of Action and Milestones (POA&M):
The POA&M document outlines the organization’s plan for addressing any unmet controls, including timelines and milestones for achieving full compliance. It is a critical component for organizations that do not achieve a perfect score initially.
4. Customer Responsibility Matrix:
This matrix delineates the responsibilities between the organization and its cloud service providers, ensuring clarity on who is accountable for various security measures.
5. Artifacts:
These are evidentiary documents that demonstrate the implementation of security controls. Artifacts can include logs, configuration files, audit reports, training records, and other evidence that supports compliance claims.
On-Premises C3PAO Assessments
Once the documentation is prepared, it is submitted to a C3PAO for review. The C3PAO will conduct a thorough on-premises assessment, which includes:
- Document Review: Evaluating the submitted documentation to verify compliance with CMMC requirements.
- Interviews: Conducting in-person interviews with key personnel responsible for IT and compliance functions. These interviews help assess the organization’s understanding and implementation of the documented controls.
- Site Visits: Performing site visits to observe and verify the implementation of security measures in the organization’s physical and IT environment.
The DoD estimates that such assessments will take approximately 120 hours with three assessors. This intensive review process ensures that the organization’s cybersecurity practices are robust and compliant with CMMC Level 2 requirements.
How PreVeil Helps with CMMC Level 2 Compliance
Achieving CMMC Level 2 compliance can be costly, complex, and time intensive. PreVeil offers a proven, three-step solution tailored for SMBs and utilized by over a thousand defense contractors. The solution not only simplifies the compliance process but also results in substantial cost savings, with organizations saving tens to hundreds of thousands of dollars. Numerous clients have successfully attained perfect 110/110 scores in their CMMC JSV assessments using this approach.
Key Benefits of Choosing PreVeil
- Significant Cost Reduction: PreVeil customers save 75% vs GCC High
- Ease of Deployment and Use: Deploys in hours alongside existing IT systems like O365, GSuite. Support for existing workflows both within the organization and with suppliers and partners, enhances compliant collaboration without added complexity.
- Unrivaled Security: Ensures top-tier protection for CUI communications.
Step 1: Secure Platform for Storing and Sharing CUI
PreVeil’s low cost, end-to-end encrypted email and file sharing solution meets CMMC Level 2 requirements, including support for NIST 800-171, FedRAMP, FIPS 140-2 encryption, and DFARS 7012 (c-g) incident reporting. It deploys in hours and integrates seamlessly with existing O365 or GSuite systems, avoiding costly replacements and minimizing deployment expenses.
Step 2: Comprehensive Documentation
PreVeil reduces the effort and cost associated with preparing for assessments by providing detailed CMMC documentation. The C3PAO validated documentation includes video tutorials that cover all 110 controls, streamlining the preparation process and significantly reducing documentation costs. Plus, get 1-on-1 support from our compliance experts if you get stuck.
Step 3: Partner Network and Expert Support
PreVeil has developed a strong network of certified CMMC consultants and MSPs to offer comprehensive compliance support, ensuring customers are fully prepared for assessments.
- Consulting Services: Expert CMMC guidance throughout the compliance journey, from assessment to certification.
- Managed Service Providers: Any external IT support required to maintain compliance.
- C3PAO Pre-Validation: PreVeil’s consistent collaboration with C3PAOs enhance familiarity with PreVeil systems and streamline the assessment process, further reducing costs and minimizing assessment risks.
Additional Resources
For further information, see more resources from PreVeil below.