The wait is over: The CMMC Final Rule (48 CFR) was published in the Federal Register on Sept 10, 2025 and CMMC requirements can be added to DoD contracts, RFPs, & RFIs starting November 10, 2025.
What 48 CFR Enforcement Means
The 48 CFR rule is the enforcement portion of the CMMC program. While the foundational CMMC Program Rule (32 CFR Part 170) has been in effect since December 2024, the 48 CFR rule transforms CMMC into a binding contractual requirement.
Here are the key take-aways for 48 CFR:
- CMMC requirements will now be added to contracts, RFPs or RFIs starting November 10, 2025 via the DFARS 7021 clause and those requirements are enforceable. Defense contractors that do not meet these assessment mandates will be disqualified from contract awards.
- This will begin a phased rollout, with Phase 1 lasting 1 year, and the number of contracts mandating compliance increasing every year.
- During Phase I, contracting officers may require defense contractors to pass a C3PAO-led assessment to be eligible for a contract. In other cases, contractors handling CUI will be allowed to self-assess to confirm their compliance with CMMC level 2.
- Contractors need to ensure that all their subcontractors have the appropriate CMMC level prior to awarding a subcontract.
- Contractors will need to maintain CMMC compliance for the life of the contract.
Want to skip the details & get help? Our sales team can walk you through the steps you need to take, or schedule a free 15 minute call with our compliance team.
CMMC Timeline and Rollout

The CMMC program will enter contracts in four phases now that 48 CFR has entered the federal register. Each phase will last a year:
Phase 1 (Q4 2025): Phase 1 will require CMMC level 2 compliance in some contracts. It’s impossible to know which contracts will be subject to the requirements until they’re released.
Organizations wishing to participate in these contracts will need to undergo a self-assessment and certify that they meet CMMC Level 2. At the same time, organizations should also use this time to prepare for a C3PAO-led assessment.
Contracting Officers do have the option during this period of including requirements for C3PAO assessments at any time to any existing contract, RFP, or RFI.
Phases 2-4: The number of contracts requiring Level 2 compliance will increase each year, with all applicable contracts mandating CMMC certification by Phase 4.
Requirements for CMMC Level 2
With Q4 2025 rollout underway, understanding Level 2 requirements is critical for planning your compliance strategy. Here are the six key areas you’ll need to address:
1. Meet NIST 800-171 Requirements
OSCs must implement all 110 NIST 800-171 controls to safeguard CUI and post their score in the Supplier Performance Risk System (SPRS). Key focus areas include access control, incident response, and physical security.
As noted above, organizations must maintain compliance with these controls throughout the life of the contract. A senior official at the contracting organization must affirm on an annual basis that their company continues to meet the CMMC compliance requirements.
2. Achieve a Minimum Score of 88
While organizations may defer some non-critical, 1-point controls, the ability to use POAMs is limited and those POAMs must be completed within 180 days. Most controls must be fully implemented before certification can be achieved.
3. Cloud Service Providers (CSPs)
If an OSC uses a CSP to store, process, or transmit CUI, the CSP must meet FedRAMP Moderate Baseline Equivalent requirements as specified by the DoD in its December 21, 2023 equivalency memo or have an official Authorization to Operate (ATO). CSPs that only provide services categorized as Security Protection Assets (SPAs) are exempt from FedRAMP requirements but will fall within the organization’s compliance boundary and be subject to their assessment.
4. External Service Providers (ESP)
If ESPs such as Managed Service Providers (MSPs), deliver services that function as Security Protection Assets—like SIEM services, antivirus, or multi-factor authentication (MFA)—those services will fall within the organization’s compliance boundary and be subject to assessment. In these cases, the MSP is not required to obtain a separate CMMC certification, as the responsibility for compliance lies with the organization utilizing those services.
5. Flow-Down Requirements for Subcontractors
CMMC imposes flow-down obligations, meaning all subcontractors handling CUI must adhere to the same cybersecurity standards as prime contractors, ensuring protection throughout the supply chain.
6. Virtual Desktop Infrastructure (VDI) Clarifications
The final rule clarifies that host computers accessing and displaying CUI from a CMMC-compliant VDI environment via Keyboard, Video, or Mouse (KVM) may be considered out of scope for CMMC assessments. However, the VDI configuration itself is in scope and must comply fully with CMMC, including meeting applicable endpoint controls.
Behind the Curve? How to Fast-Track CMMC
With CMMC requirements entering contracts in the next few weeks , organizations that aren’t compliant need to expedite their efforts to demonstrate compliance, or risk losing existing contracts and future opportunities.
If you’re not sure where to start, read our CMMC Guide. For convenience, here are 4 key ways to expedite your compliance journey:
- Limit your Compliance Boundary with an Enclave: You can establish a secure, isolated environment for CUI – known as an enclave- which simplifies your documentation & saves you money.
- Use Pre-filled Documentation: Protecting CUI is at the core of NIST 800-171 and CMMC compliance. However, you also must provide detailed documentation to your CMMC Assessor to prove that you’re compliant. PreVeil offers pre-filled, assessment-validated documentation that covers all 110 controls, including a System Security Plan (SSP).
- Limit POA&MS: Plans of Actions & Milestones (POAMs) describe your plan to meet any controls that are currently unmet. Make sure you are taking steps to address any POAMs and specifying the technologies and procedures you will need to close those gaps. C3PAOs will allow for only a limited use of POAMs at the time of assessment and then only for the least critical controls. You will need a minimum score of 80% (88/110) to be eligible for a conditional certification so we do not recommend relying on POAMs to pass CMMC.
- Leverage Partners: If you get stuck, or don’t have the time or expertise to complete the steps required, take advantage of PreVeil’s preferred network of Assessors, Consultants, and Service Providers. They offer a variety of services to help accelerate your compliance journey, and you can have confidence that they were vetted and recommended by the PreVeil compliance team.
Get Caught Up with PreVeil
If your organization wishes to stay in the Defense Industrial Base, then you will need to become CMMC compliant. PreVeil can help.
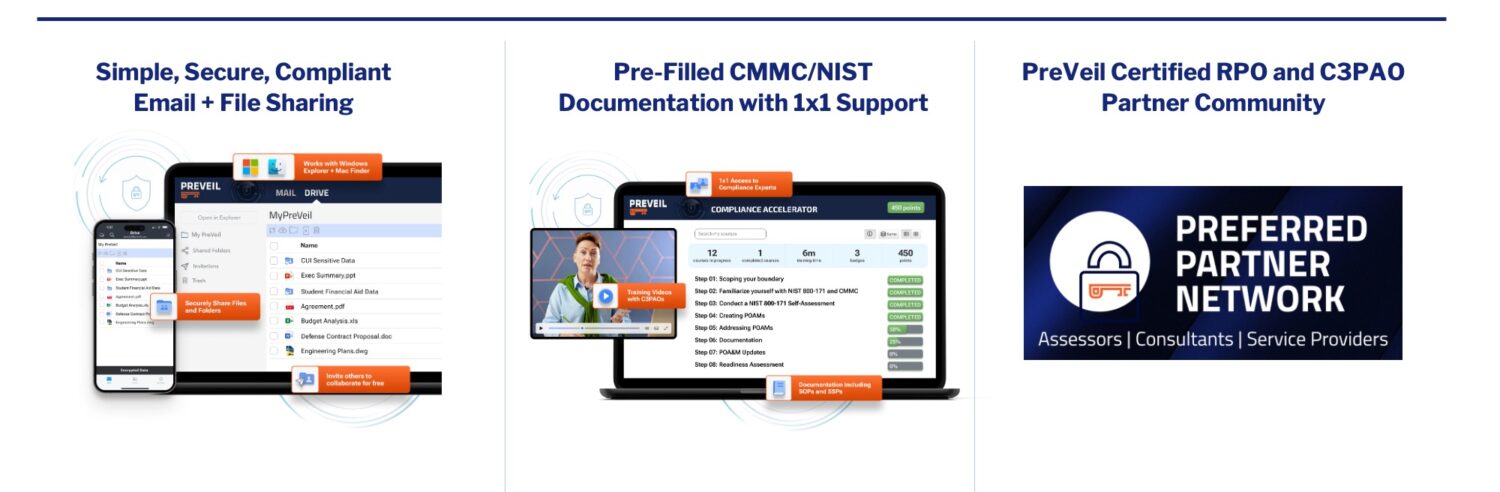
PreVeil is used by over 2,500 defense contractors and provides a comprehensive solution to expedite CMMC compliance. It includes:
- Technology Platform: Our Email and Drive platform protects CUI with end-to-end encryption and meets FedRAMP Moderate Equivalent, FIPS 140-2 and DFARS 7012 c-g.
- Compliance Accelerator: We provide pre-filled CMMC documentation, assessor-validated videos and 1×1 support from our compliance experts.
- Partner Network: We support your organization through the entire compliance journey – from prep to assessment – with our network of CMMC consultants and auditors.
PreVeil’s proven solution has been used by 75 defense contractors and C3PAOs to achieve perfect 110 scores in CMMC assessments.
Get a
PreVeil Demo
See how PreVeil simplifies CMMC
Schedule a free
Compliance Call
Get answers to your CMMC questions
Download Our
CMMC Guide
Achieve your CMMC compliance goals
To learn more, summarize in AI: