With the finalization of CMMC, which will soon integrate into defense contracts via DFARS 7021, it’s crucial for contractors to not overlook the ongoing critical role of DFARS 7012. DFARS 7012 (Safeguarding Covered Defense Information and Cyber Incident Reporting) regulations mandate the protection of Controlled Unclassified Information (CUI) and ties directly into the broader cybersecurity framework by requiring contractors to implement the 110 security controls of NIST 800-171. As defense industry standards evolve, the inclusion of a DFARS 7012 clause in contracts remains a primary indicator of a contractor’s requirement for compliance readiness.
This blog explains what DFARS 252.204-7012 is, who needs to comply, and how to make compliance simpler and more affordable.

What is DFARS 252.204-7012?
DFARS 252.204-7012 is a key clause within the Defense Federal Acquisition Regulation Supplement, and is crucial for securing Controlled Unclassified Information (CUI) in the defense sector. All contractors that handle unclassified Covered Unclassified Information (CUI)—i.e., Contractor Proprietary Information, Controlled Technical Information, and Controlled Defense Information (CDI)— will have a DFARS 7012 clause in their contract and therefore must comply with its provisions. That’s been the case since 2017. The regulation requires defense contractors and subcontractors to implement robust cybersecurity practices to protect sensitive data from cyber threats.
The essence of DFARS 7012 mandates compliance with specific cybersecurity standards, particularly those defined by the National Institute of Standards and Technology (NIST). The core requirement is adherence to NIST SP 800-171, which includes a comprehensive set of security controls for non-federal information systems.
We recommend that you review your organization’s contract to check if it contains the DFARS 7012 clause, in which case you need to comply with it. Note that your contract may be with another organization above you in the defense supply chain, rather than directly with your Prime contractor. In either case, you will still need to adhere to the requirements spelled out in DFARS 7012. Learn more below.
DFARS 7012 Requirements
DFARS 7012 outlines several key requirements essential for safeguarding Controlled Unclassified Information (CUI). This is a list of requirements that are mandatory for all defense contractors and subcontractors handling such information.
- Protect unclassified Covered Defense Information (CDI) in accordance with NIST 800-171. To provide adequate security, contractors must implement the 110 security controls stipulated in the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 as well as the 320 objectives that are part of the controls..
- Report any cyber incidents to the DoD and provide access to servers and logs, per clauses (c)-(g). Contractors need to report all cyber incidents (even commercial attacks) to the DoD Cyber Crimes Center (DC3), share all cyber incident data, retain that data for 90 days, and assist DC3 with any follow up investigations as needed. See the (c)-(g) section below, which specifies these requirements.
- Ensure Cloud Service Providers (CSPs) Meet FedRAMP Moderate or Equivalent standards. Contractors must confirm that their CSPs have achieved the Federal Risk and Authorization Management Program (FedRAMP) Baseline Moderate or Equivalent standard. PreVeil is the first CSP to meet this stringent FedRAMP Moderate Equivalency requirement for CMMC and DFARS 7012 compliance.
Note that the DFARS 7012 clause also requires defense contractors to flow down all the 7012 requirements to their subcontractors.
How DFARS 7012 Overlaps with CMMC and NIST 800-171
DFARS 7012 requires implementation of the 110 security controls specified in NIST SP 800-171. CMMC Level 2—the minimum level that must be attained by contractors that handle CUI—will require compliance with the same 110 NIST SP 800-171 security controls. The key difference is that under CMMC, compliance will be checked by independent third-party assessors (C3PAOs) certified by the CyberAB, the CMMC Accreditation Body.

As Stacy Bostjanik (Chief Defense Industrial Base Cybersecurity, U.S. Department of Defense) said during PreVeil’s CMMC Summit, “CMMC is just the validation program that people have done what they already agreed to do in complying and establishing the requirements of NIST 800-171 in their current networks.”
How DFARS 7019, 7020, and 7021 build on DFARS 7012
The DoD released its DFARS Interim Rule, formally known as the Defense Federal Acquisition Regulation Supplement: Assessing Contractor Implementation of Cybersecurity Requirements in 2020. The goal of this supplement was to increase compliance with DFARS 7012. The Interim Rule introduced three new clauses – 7019, 7020 and 7021.
- Clause 7019 dramatically strengthens DFARS 7012 by requiring that contractors conduct a NIST SP 800-171 self-assessment according to DoD Assessment Methodology. Further, self-assessment scores must be reported to the DoD via its Supplier Performance Risk System (SPRS). SPRS scores must be submitted by the time of contract award and not be more than three years old.
- Clause 7020 notifies contractors that the DoD reserves the right to conduct a higher-level assessment of contractors’ cybersecurity compliance, and that contractors must give DoD assessors full access to their facilities, systems, and personnel. Further, 7020 strengthens 7012’s flow down requirements by holding contractors responsible for confirming that their subcontractors have SPRS scores on file prior to awarding them contracts.
- Clause 7021 paves the way for rollout of the DoD’s Cybersecurity Maturity Model Certification (CMMC) program. The CMMC Proposed Rule became law in December 2024 and it will appear in contracts in late 2025. Visit our CMMC Timeline blog for the latest updates. 7021 also stipulates that contractors will be responsible for flowing down the CMMC requirements to their subcontractors.
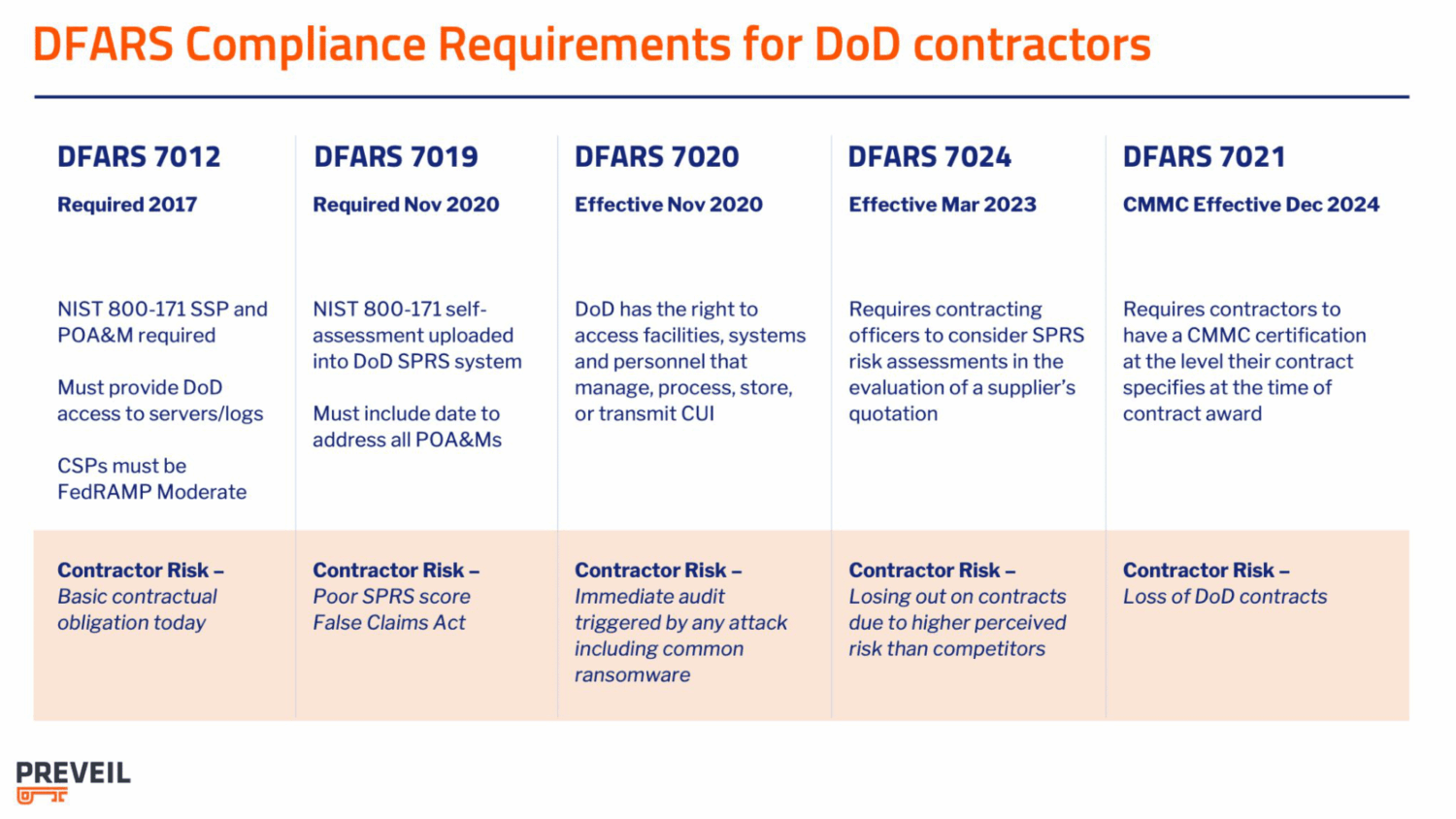
DFARS 7012 Non-Compliance Risks
Noncompliance with DFARS 7012 poses significant business risks. Cyber criminals often target smaller organizations, which they perceive as more vulnerable compared to well-resourced prime contractors. The consequences of such vulnerabilities can be severe, including the loss of intellectual property, operational incapacity, and substantial recovery costs that might include ransomware payments.
Furthermore, DFARS 7012 mandates that all cyber incidents be reported to the Department of Defense (DoD). Should investigations reveal inadequate security measures—essentially a failure to comply with the DFARS 7012 contract clause—the DoD may view this as a contract breach. Potential corrective actions can be severe and include:
- Withholding of progress payments
- Foregoing remaining contract options
- Contract termination, either partially or completely
DFARS 252.204-7012 Checklist
- Reduce your compliance boundary: If only a portion of your organization handles CUI, then it makes sense to narrow the scope of the security requirements by creating a separate enclave. This translates into a simpler assessment process that saves you time and money. Some solutions like Microsoft GCC High often need to be deployed across entire organizations, adding significant costs and complexity.
- Choose a platform that’s easy to use and deploy: Platforms like Microsoft GCC High often require expensive consultants, separate email addresses, and a full rip-and-replace. Look for a solution that can be deployed in hours, uses your existing email addresses, and integrates directly with the tools you’re already using, like Outlook, Gmail, File Explorer and MacFinder.
- Deploy a solution with proven CMMC credentials: If your organization has migrated to the cloud, know that standard commercial cloud services such as Microsoft 365 Commercial do not meet CMMC requirements for storing, processing and transmitting CUI. You want to verify that it has FIPS 140-2 encryption modules, meets DFARS c-g, is FedRAMP Moderate or Equivalent, and has been used to pass multiple DoD assessments.
- Use pre-filled compliance documentation to save you time and money: To pass an assessment, contractors will need detailed, evidence based documentation clarifying how the controls are addressed within their company. This can be a daunting, time-consuming and costly task so look for a solution that offers pre-filled documentation including a System Security Plan (SSP) and Standard Operating Procedures.
DFARS 7012 FAQs
Are DFARs 7012 and NIST SP 800-171 the same?
No, they are not the same, but they are closely linked. DFARS 7012 is a DoD contract clause that requires contractors to protect Covered Defense Information (CDI). One of its core requirements is implementing the security controls outlined in NIST SP 800-171.
When does DFARS 7012 flow down to subcontractors?
DFARS 7012 flows down to subcontractors when they handle Covered Defense Information (CDI) under a DoD contract. Prime contractors are responsible for ensuring the clause is included in applicable subcontracts. If no CDI is shared, the clause does not apply.
Conclusion
PreVeil is the leading solution for DFARS 7012, NIST 800-171 and CMMC compliance and is trusted by more than 2,000 small and midsize defense contractors. In addition, over 50 PreVeil customers have achieved compliance with DFARS 7012/CMMC- validated by a perfect 110 score on their C3PAO or DoD assessment.