Endpoint security is the practice of protecting network-connected devices from cyber threats and unauthorized access. For organizations handling Controlled Unclassified Information (CUI), endpoint protection is not just good practice—it’s a regulatory necessity under frameworks like NIST SP 800-171 and CMMC compliance.
This guide provides a complete overview of endpoint security requirements, from identifying endpoints to securing them with assessor-approved tools and configurations.
What are Endpoint Devices?
Endpoint devices are any hardware components that connect to and interact with your organization’s network. Each endpoint represents a potential entry point for attackers, making them a critical part of your security perimeter.
Endpoints typically run operating systems like Windows, macOS, Linux, iOS, or Android and can store or process sensitive information.
Endpoint Device Examples
- Workstations & Laptops – Often the primary work tools; they handle most sensitive document storage and processing.
- Mobile Devices (Smartphones, Tablets) – Used for email, messaging, and file sharing, often outside the corporate network.
- Virtual Endpoints – Virtual Desktop Infrastructure (VDI) and cloud-hosted desktops; still require the same security controls.
- IoT Devices – Printers, cameras, and smart devices connected to your network.
- External Storage Devices – USB drives and portable SSDs; must be encrypted to protect data in transit.
How to Manage Endpoint Security
Effective endpoint security requires both technical safeguards and administrative controls, but these endpoint security measures should not be difficult to implement. In fact, PreVeil’s Compliance Accelerator walks contractors through the exact tools & configurations that have enabled over 75 customers to achieve CMMC compliance. Here are some endpoint security practices that align with CMMC Level 2 and NIST SP 800-171 requirements:
- Mobile Device Management (MDM): MDM platforms such as Microsoft Intune, Google Endpoint Management, or VMware Workspace ONE allow IT teams to enforce consistent security baselines across laptops, smartphones, and tablets. These solutions provide centralized control over device settings, ensuring that full-disk encryption is enabled, operating systems are patched, and lost or stolen devices can be remotely wiped. MDM is also essential for maintaining an accurate endpoint inventory, which auditors frequently require for compliance.
- Anti-Malware & Endpoint Detection and Response (EDR): Traditional antivirus alone is no longer enough to protect against sophisticated threats. Modern solutions like Microsoft Defender for Endpoint, CrowdStrike Falcon, and SentinelOne combine signature-based detection with behavioral analytics to identify and stop advanced malware and ransomware. EDR platforms add visibility into suspicious processes, isolate compromised endpoints, and enable incident response teams to take immediate action.
- Full-Disk Encryption (FDE): Data stored on endpoints must be encrypted at rest using FIPS 140-3 validated algorithms, a strict requirement for NIST 800-171 and CMMC. On Windows devices, this means enabling BitLocker with TPM integration and AES-256 encryption; on macOS, FileVault 2 with XTS-AES-256. MDM tools can escrow encryption keys to ensure they are recoverable if users forget their passwords. Without FDE, sensitive information on a stolen device could easily be compromised.
- Multi-Factor Authentication (MFA): Passwords alone cannot protect sensitive data. Adding MFA—via apps like Microsoft Authenticator, Duo, or hardware tokens like YubiKey—ensures that only authorized users can access endpoints, especially in remote work environments. MFA is required for privileged accounts, administrative access, and any user handling Controlled Unclassified Information (CUI). Implementing MFA significantly reduces the risk of credential theft and unauthorized access.
- Security Information and Event Management (SIEM): Compliance frameworks require organizations to log endpoint activity and monitor it for anomalies. Tools like Microsoft Sentinel, Splunk, or Elastic SIEM aggregate logs from all endpoints and correlate events in real-time. This makes it possible to detect unauthorized access attempts, malware outbreaks, or unusual login activity. A properly configured SIEM not only strengthens security but also provides auditors with evidence of continuous monitoring.
- Vulnerability Management: Endpoints must be scanned regularly for unpatched software and configuration weaknesses. Vulnerability management platforms such as Tenable Nessus and Rapid7 InsightVM identify high-risk Common Vulnerabilities and Exposures (CVEs) and provide remediation guidance. Best practice is to patch critical vulnerabilities within 15 days, in line with DoD and NIST guidelines. Automated vulnerability scans ensure organizations stay ahead of emerging threats and maintain compliance.
Endpoint Security Checklist
| Control Category | Requirement for Compliance | Notes |
| Anti-Virus/EDR | Required on all endpoints | Must be centrally managed and updated daily |
| Full-Disk Encryption | FIPS 140-3 validated encryption enabled | Ensure vendors validated through CMVP |
| MFA | Enforced for all privileged and remote accounts | Can integrate with SSO |
| Logging & Monitoring | SIEM integration for event correlation | Retain logs ≥ 90 Days |
| Device Inventory | Real-time asset tracking through MDM | Must include serial numbers and OS versions |
| Vulnerability Scanning | Scheduled scans with remediation tracking | High-risk CVEs patched within 15 days |
Endpoint Security Compliance for CMMC & NIST
NIST SP 800-171 requires security controls for all systems that store, process, or transmit CUI. CMMC Level 2 builds on these controls by enforcing third-party assessments to verify compliance.
Key NIST 800-171 Controls Related to Endpoints:
- 3.1.12: Monitor remote access sessions.
- 3.4.6: Employ cryptographic protections (FIPS 140-3).
- 3.13.8: Protect against malicious code.
- 3.14.1: Identify, report, and correct system flaws.
CMMC Level 2 & Endpoints:
- Requires implementing all 110 NIST 800-171 practices.
- Endpoint-specific controls often require demonstrable logs, policies, and configuration evidence during an audit.
Endpoint Security Solutions
Choosing the right endpoint security solution set is key to both security and compliance. Some platforms include:
- Microsoft Defender + Intune – Unified threat protection and device management.
- CrowdStrike Falcon – Lightweight EDR with AI-driven threat detection.
- SentinelOne Singularity – Autonomous AI response to endpoint threats.
- Tenable Nessus – Vulnerability assessment for patch prioritization.
- Splunk Enterprise Security – High-powered log aggregation and threat hunting.
Advanced Endpoint Security Best Practices
- Zero Trust Architecture – Treat every endpoint as untrusted until verified.
- Least Privilege Access – Limit endpoint users to only the permissions required.
- Application Whitelisting – Allow only pre-approved applications to run.
- USB Port Control – Disable or restrict removable media unless encrypted.
- Geofencing Policies – Block logins from outside approved locations.
Simplifying Endpoint & CMMC Compliance with PreVeil
Organizations still face the challenge of correctly configuring the solutions listed above to ensure they meet compliance requirements and that the solutions integrate with one another.
That’s why PreVeil created a new Compliant Endpoint Configuration module, the latest addition to our Compliance Accelerator.
This module includes detailed instructions, screenshots, and videos with step-by-step instructions on how to correctly configure your technologies.
For example, to enable Multifactor Authentication (MFA) in Bitlocker the Compliant Endpoint Configuration module instructs users to:
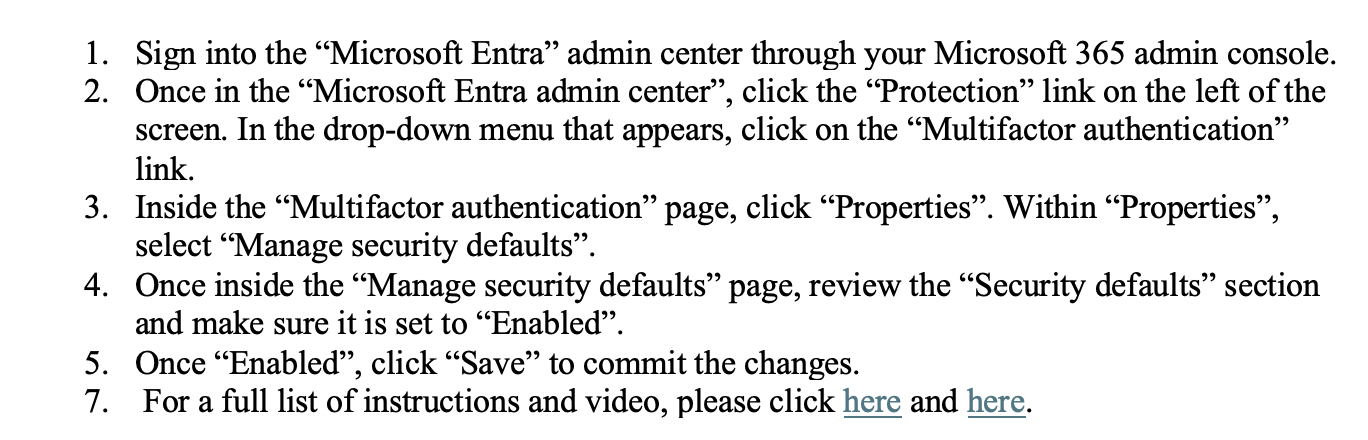
And this level of detailed instruction is available for each aspect of endpoint protection required by CMMC. With this level of instruction, you can save your team hundreds of hours and ensure you are correctly deploying your endpoint protection. In fact, 75 contractors using PreVeil have achieved 110/110 on CMMC assessments, often in under six months.
Conclusion
Securing your endpoints is a crucial step in achieving full compliance after deploying PreVeil or any other email/file sharing solution. The Compliant Endpoint Configuration module in our Compliance Accelerator vastly simplifies the process, saving you thousands of dollars and cutting your preparation time in half.
Having the PreVeil Compliance Accelerator package is what made compliance and documentation not as big of a burden. We got a topnotch Shared Responsibility Matrix and System Security Plan from PreVeil that we used as our base. … And that covered a lot of our work.
– VP of IT at a $300M Technical Consulting Firm