Public-private key encryption is a method of cryptology that uses two related keys to protect important data. One of the keys is a public key that is known to everyone and the second key is a private key that is only known to its owner. These, two unique cryptographic keys work together to guard digital information from prying eyes and keep your email encrypted.
In this blog post, we will dive into how public and private keys work, how they are used and their benefits.

Table of contents
Public-Private Key Encryption Explained
In public-private key cryptography, the public key and private key work together to ensure the security of the exchanged data. A message gets encrypted by a public key, which is available to everyone, and can only be decrypted with its unique private key,which is only available to its owner.
Public keys have been described by some as being like a business’ physical address – it’s public and anyone can look it up and share it widely. In asymmetric encryption, public keys can be shared with everyone in the system. Once the sender has the public key, he uses it to encrypt his message.
Each public key comes paired with a unique private key. Think of a private key as akin to the key to the front door of a business where only you have a copy. This defines the main difference between the two types of keys. The private key ensures only you can get through the front door. In the case of encrypted messages, you use this private key to decrypt messages.
How are keys generated?
The keys discussed here are not really keys at all, but rather large prime numbers that are mathematically related to one another. In this case, being “related” means that whatever is encrypted by the public key can only be decrypted by the related private key.
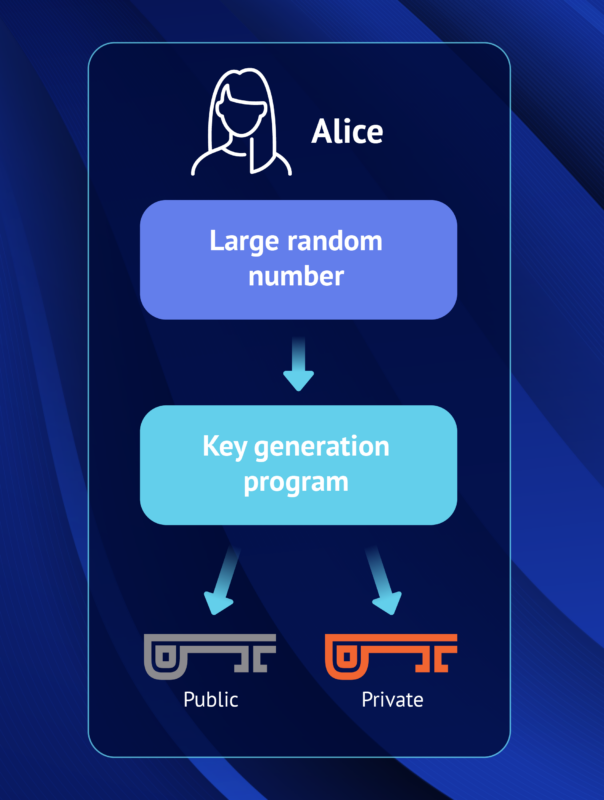
The private key cannot be guessed based on the public key. Because of this, a public key can be freely shared without threat of attack. The private key, in contrast, belongs to only one person.
Examples
Here’s an example of how these keys work together.
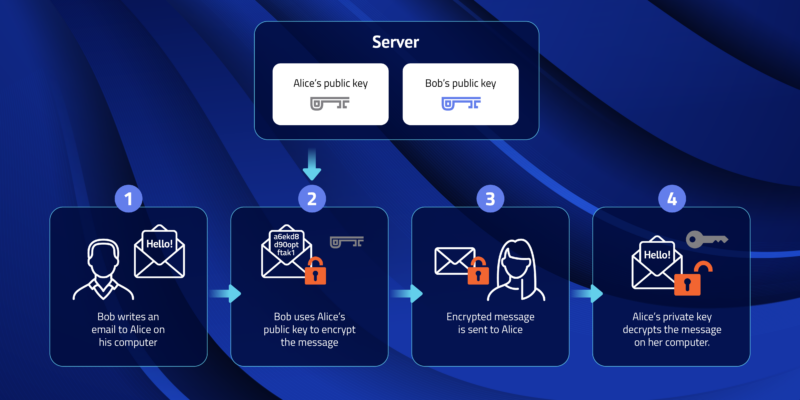
Bob wants to send Alice an encrypted email. To do this, Bob takes Alice’s public key and encrypts his message to her. When Alice receives the message, she uses the matching private key that is known only to her in order to decrypt the message from Bob.
Attackers might try to compromise the server in order to access the encrypted information, but they will be unable to because they lack the private key to decrypt the message. Alice is the only one who possesses the private key, and therefore is the only one able to successfully decrypt and access the message. When Alice wants to reply to Bob’s message, she simply repeats the process by encrypting her message to Bob using Bob’s public key.
There are several popular mathematical algorithms that are used to generate the public and private keys. Some well-respected algorithms include:
- Rivest-Shamir-Adelman (RSA): Oldest of the public-private key cryptography systems. Frequently used to transmit shared keys for symmetric key cryptography.
- Digital Signature Standard (DSS): A Federal Information Processing Standard specifying the algorithms that can be used to generate digital signatures used by NIST.
- Elliptic curve cryptography (ECC): As its name implies, ECC relies on elliptic curves to generate keys. It is often used for key agreements and digital signatures. At PreVeil, we use elliptic-curve cryptography’s Curve-25519 and NIST P-256.
All of these encryption methods are able to generate asymmetric key pairs of various sizes.
Uses of Public and Private Key Encryption
There are several popular mathematical algorithms that are used to generate the public and private keys. Some well-respected algorithms include:
1. Digital Signatures: Public keys can sometimes be used to decrypt a private key. This is the logic behind the creation of digital signatures, which are used to assure that the person sending the message is who they claim to be.
Typically, the recipient’s public key is used to encrypt the data and the recipient then uses their private key to decrypt the data. However, with this form of messaging there is no way to authenticate the source of the message. Mike could get a hold of Alice’s public key (since it’s public) and send an end-to-end encrypted message to Alice while pretending to be Bob. These are referred to as man-in-the-middle attacks.
Using a digital signature security scheme, Alice would know not to trust the origin of the message unless the message is accompanied by a digital signature unique to the sender. In this case, Alice would look for Bob’s digital signature. If there is no digital signature to ensure that Bob is the sender, Alice can act with caution knowing that it could be anyone (like Mike, for example) sending the message under Bob’s name.
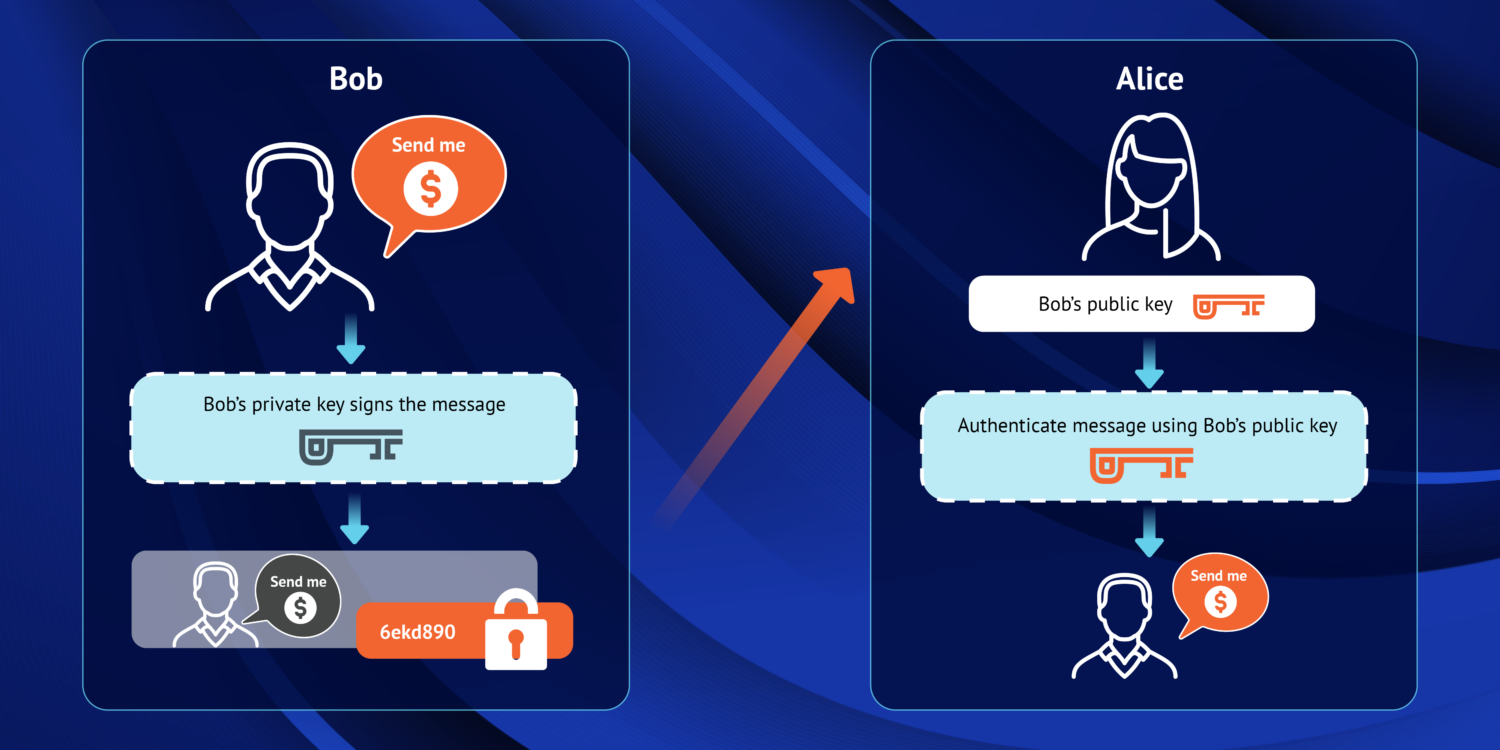
To create a digital signature, Bob digitally signs his email to Alice using his private key. When Alice receives the message from Bob, she can verify the digital signature on the message came from Bob by using his public key. As the digital signature uses Bob’s private key, Bob is the only person who can create the signature. If the digital signature is present and it matches Bob’s public key, Alice can proceed with confidence that the sender is in fact Bob.
2. Diffie-Helman Key Exchange: The Diffie Hellman key exchange demonstrates how users can securely exchange cryptographic keys over a public channel.
In the past, secure encrypted communication required that the individuals first exchange keys by a secure means such as paper key lists transported by a trusted courier. The Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure channel by establishing a shared secret. This key can then be used to secure communications.
PreVeil uses the Diffie-Hellman key exchange to enable Web PreVeil. Web PreVeil is a browser based end-to-end encrypted email service that allows users to easily access their secure email account on the web without any software downloads or any passwords to remember.
Differences between public and private keys
The primary difference between public and private keys are summarized in the table below:
Benefits of public private key
By using a public and private key for encryption and decryption, recipients can be confident that the data is what the sender says it is and the sender is who they say they are. The recipient is assured of the confidentiality, integrity, and authenticity of data exchange.
Confidentiality is ensured because the content secured with the public key can only be decrypted with the private key, so that only the intended recipient access the information.
Integrity is ensured because the decryption process includes the step of checking that the received message matches the sent message. This validates that the message has not been changed in transit.
Authenticity is ensured because each message is digitally signed using the sender’s private key. The only way to decrypt that private key is with the corresponding public key, which the recipient can access. By signing the message with the sender’s private key, this guarantees for the recipient that the message really did come from the sender.</p>
How PreVeil Harnesses the Strength of Keys
PreVeil leverages the power of the public-private keys to provide unbeatable data security through end-to-end encryption. With this advanced cryptographic system, messages and attachments are encrypted on the sender’s device using the recipient’s public key. Want to learn more? Contact Us today.
The encrypted data can only be decrypted on the recipient’s device with their corresponding private key, so that sensitive information remains confidential throughout transmission and storage. By eliminating the a central point of attack while data is in transit or at rest on the server, PreVeil’s end-to-end encryption offers robust protection against unauthorized access and interception.
With user-friendly features like automatic key management and secure logs, PreVeil ensures that security doesn’t compromise usability. With PreVeil’s end-to-end encryption service, organizations and individuals can rest assured that their data is protected at all times.