What is end-to-end encryption?
End-to-end encryption (E2EE) is a secure way to transfer data from one user’s device to a recipient’s device while hiding the information from any intermediary, such as a mail service provider. With E2EE, data is encrypted on the sender’s device and is only ever decrypted on the recipient’s device – never in the cloud — because only the sender and recipient possess the keys to encrypt and decrypt the message. As a result, attackers watching Internet traffic or breaching a server cannot access the data.
PreVeil as well as popular messaging apps such as iMessage, WhatsApp, and Signal use end-to-end encryption to protect their users’ data.
Overview of Encryption Techniques
- Encryption in Transit: Encryption in transit prevents an eavesdropper from watching traffic across the Internet. Most email systems and browsers use the SSL/TLS algorithm to encrypt traffic as it traverses the Internet from device (phone or computer) to server and back. The data is decrypted at each end.
- Encryption at Rest: Many computer operating systems like Mac OS and Windows offer “full disk encryption,” which means that files are encrypted on disk when they’re not being used. This prevents someone who physically steals a computer from accessing the information on the disk because the user needs to successfully log in to the computer in order to decrypt the data.
- End-to-End Encryption: E2EE data is encrypted in transit from device to server. Furthermore, the data stays encrypted until it reaches the recipient’s device. It therefore protects not only against intruders watching data flow across the internet, but attackers who can penetrate the server as well.
How does end-to-end encryption work?
Encryption works by encrypting (scrambling) data so that only someone with the specific secret number (called the key) can unscramble it. With end-to-end encryption, this scrambling and unscrambling process works by using a unique pair of keys to encrypt and decrypt a message. One of the keys in the pair is used only for encryption and the other is used for decryption.
When someone wishes to send an email or file, the information is encrypted on the sender’s device (computer or smartphone) by retrieving the recipient’s encryption key which is stored in the cloud. This encryption key is called a public key because it can be shared safely with everyone as it can only be used to encrypt data. The corresponding decryption key is kept only by the message recipient, and it’s called a private key.
By storing the user’s private key on their device, the key is never available to the cloud. Since the cloud cannot access decryption keys, it can never decrypt data, which means that criminals and nosy third parties who try to attack the cloud servers cannot see the data either. Since the most damaging attacks often involve cloud servers, E2EE offers individuals and businesses a powerful way to exchange information and store sensitive data without sacrificing privacy or security.
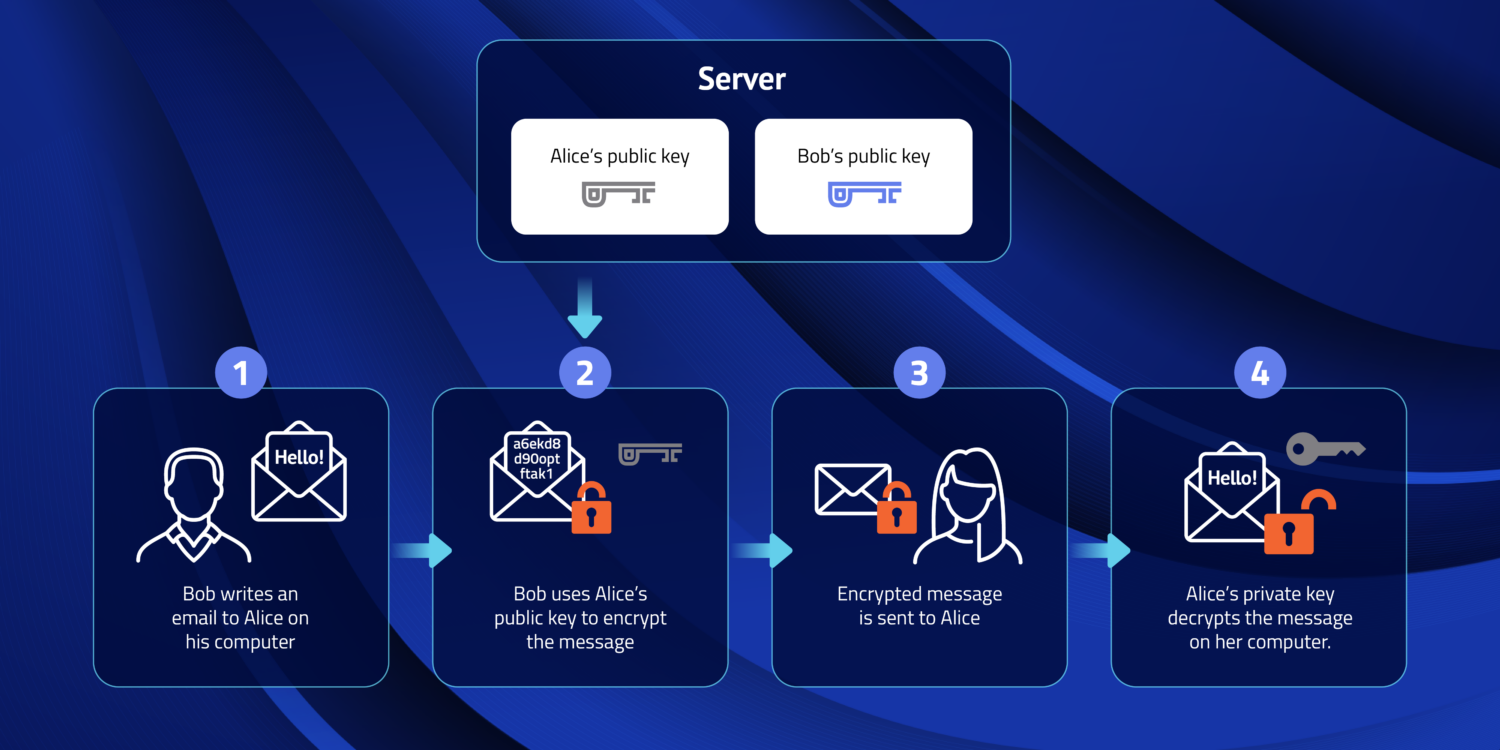
End-to-End Encryption Example
Let’s take an example of Alice and Bob who want to exchange messages using an E2EE system. The system provides each with a public/private key pair, and their public keys are stored in the cloud. Their private keys are stored on their devices.
Bob wants to send Alice an encrypted message. His device’s software retrieves Alice’s public key from the cloud and uses it to encrypt his message to her. The software then sends the encrypted message to Alice’s device. When Alice’s device receives the message, it uses the private key on her device to decrypt the message from Bob. When Alice wants to reply, she repeats the process, encrypting her message to Bob using Bob’s public key.
Because the information is encrypted before it leaves one device and not decrypted until delivered to the recipient nobody in the middle — neither an internet service provider, mail service, or malicious actor listening to the Internet or penetrating any of the systems involved —can access the data.
Find out how PreVeil can assist with End-to-End Encryption
What E2EE technologies are used in email systems?
Here are several approaches to end-to-end encryption that have been developed over the years:
- PGP: Pretty Good Privacy (PGP), was one of the first forms of end-to-end encryption. It uses public/private key pairs to encrypt messages for a specific recipient. It hasn’t received significant traction because it relies on users to set up and exchange keys, which most users find cumbersome.
- S/MIME: Another popular end-to-end encryption technique is Secure/Multipurpose Internet Mail Extensions (S/MIME). S/MIME also uses public/private key pairs. The public key is packaged in a “certificate” which also includes other information about the sender and a verification that the sender is the owner of the public key, and the certificate is included in the email message. S/MIME also allows messages to be digitally “signed,” which provides cryptographic proof that the message has not been tampered with during transmission. While S/MIME certificates are better supported by many email systems than PGP, it still can be cumbersome to use unless set up and managed by IT administrators.
- PreVeil E2EE: The PreVeil system uses end-to-end encryption with public and private keys managed by the system itself instead of requiring users or administrators to do so. This results in the security provided by end-to-end encryption but with the simplicity of using a standard mail client (like Outlook, Gmail, or Mac Mail) without the extra IT or user overhead in managing keys and certificates.
What are the benefits of E2EE?
End-to-end encryption provides several crucial benefits that make it a powerful tool for data security, protecting against the most invasive threats, and facilitating compliance with regulatory standards.
- Protection of Data Against Transmission, Server, and Data Center compromises: The most devastating cyber-attacks often occur when a server is compromised because the attacker can then access all the information stored on that server. In these situations, entire organizations or even multiple organizations are compromised with a single attack. With E2EE, data is encrypted from the time it leaves the sender’s device until it’s received by the recipient, it’s indecipherable in between these points. That means that an attacker trying to watch traffic across the Internet or an attacker able to penetrate a server in the cloud or data center will just see gibberish. So E2EE provides excellent protection against the most severe data breaches.
- Data Integrity and Tamper-Resistance: In addition to encrypting data, most E2EE systems also use cryptographic methods to “sign” documents to vouch for their integrity. The “signature” is a set of numbers that validate that the sender is who they say they are, as only the sender would have the private key that creates the signature. Furthermore, the signature also contains the result of a mathematical calculation of the contents of the data. If even a single character in a large document changes, the result of the mathematical computation will change. So, the recipient can be assured that the data was not tampered with since created by the sender.
- Regulatory Compliance: Many industries face increasing cybersecurity compliance regulations in order to combat ever escalating threats. Personally Identifiable Information (PII) must be protected in a number of industries — from education to health care (as codified in HIPAA regulations). Some of the most stringent regulations pertain national defense. For example, the US State Department’s International Traffic in Arms Regulations (ITAR) specifically mandate end-to-end encryption in order to transmit data electronically. Furthermore, the US Department of Defense is requiring that all 300,000 contractors in the US Defense Industrial Base comply with new Cybersecurity Maturity Metric Certifications (CMMC), whereby end-to-end encryption can help contractors comply with regulations that protect Controlled Unclassified Information (CUI).
What are the challenges of E2EE (can it be hacked)?
While end-to-end encryption is widely regarded as one of the most secure methods to protect data, no technology can guarantee 100% protection against any kind of threat. Here are some challenges associated with E2EE:
- Vulnerability to Compromised Endpoints: While E2EE can protect against some of the most devastating attacks, i.e. server breaches, data can still exist unencrypted on a user’s device. Therefore, an attacker that breaches a device can access its data. This can be combated by the use of endpoint security — software that looks for viruses and malware on the computer. Note that should an attacker seek to penetrate an organization that uses E2EE, the attacker will have to penetrate many devices, which is often significantly more difficult than attacking a single server.
- Access Patterns and Metadata: While servers using E2EE cannot decrypt user data — and hence an attacker penetrating the server cannot “see” the data directly — a breach of the server may reveal access patterns that can be useful to an attacker. For example, the server knows the senders and recipients of messages (and their corresponding email addresses, which is referred to as Metadata). Sometimes knowing that person A communicated with person B and time T is valuable to an attacker, and even E2EE can’t prevent this information from being leaked in a server attack.
- Limited Accessibility for Law Enforcement. In systems that don’t use E2EE, law enforcement can compel the owner of a server, which may be an email provider, to disclose information that’s contained on the server. With E2EE, all the data on the server is encrypted, so the service provider does not have the means to decrypt the data. Law enforcement must resort to methods used for physical objects, compelling the whomever owns the data to provide it.
Examples of E2EE in Commercial Products
Due to the superior security results and minimized attack surface, end-to-end encryption is quickly gaining traction across industries that rely on secure data exchange. Let’s look at real-world examples of end-to-end encryption in popular apps:
- Mobile Messaging. WhatsApp, Signal, and Apple’s iMessage all use end-to-end encryption to secure messages between individuals and groups. The implementations differ somewhat in technique, but all use public/private key pairs where the sender uses a recipient’s public key to encrypt a message that only the recipient’s private key can decipher. These messaging apps were all originally designed for mobile phones and are optimized for device-to-device communication (as opposed to user-to-user communication where a user might have multiple devices).
- Email Services. Most email apps like Outlook and Mac Mail do not use end-to-end encryption natively but can be configured to use S/MIME. As noted above, S/MIME requires certificates that are usually created and managed by IT administrators.
- PreVeil Email is an alternative that marries the advanced security of end-to-end encryption with ease of use. Public/private key pairs are used to secure messages, but they are managed automatically by the system so IT administrators don’t have to deal with the hassles of certificates. PreVeil can be used with mail clients like Outlook, Mac Mail, and Gmail and users keep their existing email address. It in essence creates a secure email garden separate from the jungle of Internet email with its phishing attacks and spam. The PreVeil system also includes Drive, a secure file storage and sharing service just like DropBox, OneDrive, or Google Drive, using end-to-end encryption to protect user data. For regulated environments, PreVeil’s security offers a cost-effective solution to secure sensitive data such as CUI and meet CMMC, ITAR, and HIPAA compliance.
To learn more, summarize in AI:
About PreVeil
PreVeil is an end-to-end encrypted system for email and file storage & sharing. PreVeil Email works with standard mail apps like Outlook, Gmail, and Mac Mail. PreVeil Drive can be accessed through Windows File Explorer and the Mac Finder. PreVeil’s security protects against password breaches, sever attacks, and rogue administrators. PreVeil is available for Windows, Macintosh, iPhone/iPad, and Android devices.
PreVeil is the leading solution for CMMC and DFARS compliance, trusted by over 2,000 defense contractors.
To learn more about PreVeil: